
05 Dec 2011
A colleague pointed me to Telex.CC, a project from the University of Michigan that proposes "a new approach to circumventing Internet censorship that is intended to help citizens of repressive governments freely access online services and information." They start from the observation that current anti-evasion techniques are really a game of cat-and-mice. When a site gets blocked, users try to access it through some proxies, but the censors will discover and block the proxies, so users get to constantly seek new proxies. Also, if a proxy is discovered, the censors can find out who is attempting to use it, and maybe tell the local police. What if there was no need for proxies? What if the proxies were somehow built in the fabric of the Internet?
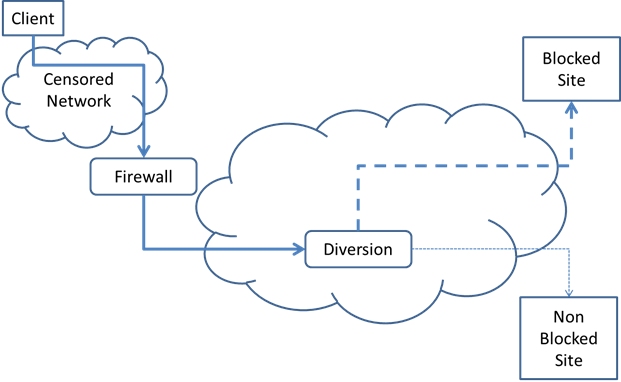
The idea is quite neat. Assume that the censor is willing to allow communication with various sites that use SSL/TLS. They have to if their country wants to continue benefiting from e-commerce over the Internet. Assume now that the user has some kind of browser plug-in that detects the blocked sites, and replaces the connection request by a connection to some other innocuous site. The connection to "https://blocked.com" will be replaced by a connection request to some other site, say "https://nonblocked.com." The TCP connection will proceed to the requested address, but the packets will then get "magically" routed to the blocked site, "https://blocked.com."

The diagram explains how the magic is possible. Somewhere on the path to the non-blocked site, the traffic encounters a "diversion" router that recognizes the original intent of the client and diverts the connection towards the blocked site. The information was carefully hidden in the HTTP header sent by the client. According to the "Telex" design, it is actually encrypted by the client using the public key of the diversion service, and then woven into the HTTP header using steganography. The censor's firewall cannot find the information, because it does not have access to the diversion service's private key.
Of course, there are some daunting engineering problems, and it is not clear that the Telex project has solved them all. Steganography is difficult to engineer in practice, and I have no idea how good the proposed solution actually is. The client software needs to maintain lists of blocked sites and adequate "non-blocked" sites, and these lists have to be somehow passed through the censor's firewall. But the greatest difficulty stems from the dynamic nature of Internet routing.
The diversion will only work if there is a diversion box on the path between the client and the "non-blocked" site. In practice, that requires either placing a lot of diversion routers in the Internet, or placing the diversion routers very close to the non-blocked sites. The latter is probably more realistic, at least during the early deployments, but that means a relatively small number of non-blocked sites. If there are few such sites, the censors may just block them. Let's hope that the Telex project can deploy enough of these boxes!